Tor, or the Onion Router, is a browsing tool used to surf the web anonymously. You may not know or care but there are many ways the Internet can track us. By using our IP address, websites are able to use identifying information to target advertising and collect data about our browsing habits. So, it’s no surprise that journalists, activists, privacy advocates and even ordinary people have turned to Tor for a more anonymous browsing experience. Long story short, if you are planning to troll people like Skankhunt42, you’ll need a more private browser than Google Chrome or Mozilla Firefox.
How Tor Protects Your Online Privacy?
In a normal Internet connection, you are directly connected to the website you’re trying to visit. This website and any other prying eyes like government, advertisers and stalkers can see who you are and that you’re trying to access their server using your IP address. Tor network, however, is made up of countless nodes or relay points that pass your data along using layers of encryption – hence the onion metaphor. Each node that your data passes through peels off another layer of encryption, showing the previous node’s IP address, as well as where it’s being sent to. Each node only decrypts not the information in the packet to know where to send it next so none of the nodes know both your identity and the identity of whatever website or server you are trying to connect to. The last node your data passes through is known as the exit node and it peels off the final layer of encryption and then delivers your data to the intended server.
Is Tor Entirely Foolproof?
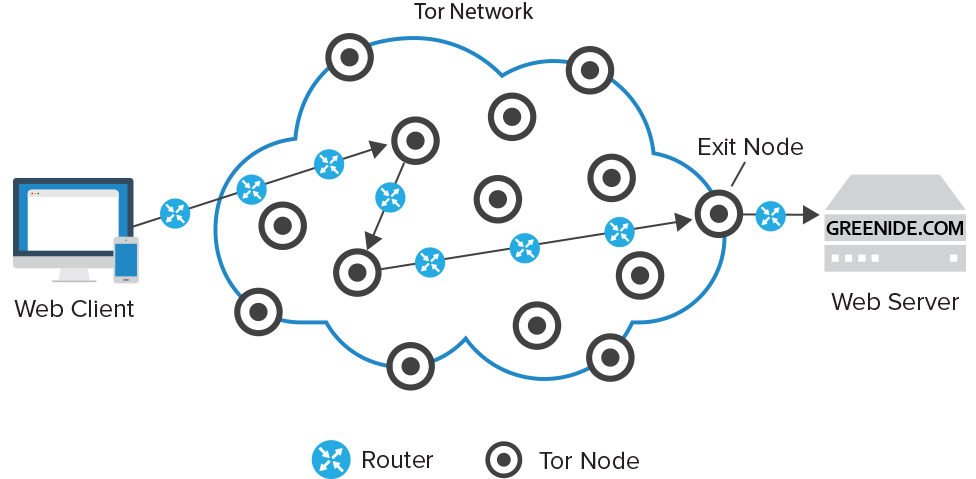
The point of origin and the intermediary nodes are completely unknown. Besides browsing the Internet, Tor users can utilize its hidden services to create private websites and messengers that can only be found using a Tor browser. These private sites, which are part of the dark web, are where pages like the Internet black market Silk Road can be found. However, not all activity on Tor is for nefarious purposes. Anonymous Internet usage can be important for journalist who are reaching out to sources, activist who live in countries that censor or block Internet usage (North Korea, Iran, Turkey, China etc.) and even law-enforcement officers who use it for undercover operations.
However, nothing is perfect and while onion routing makes it harder for hackers and spies to track your activities, it doesn’t make it impossible. There are still ways attackers can view activity on the network and extract data from vulnerable entry and exit points, especially if Tor users are not diligent and all Internet network is not monitored by Tor.
At some point, your data has to leave Tor network to get to wherever it’s going to through exit node. When your data leaves the exit node and is sent to its destination, it is no longer necessarily encrypted. As soon as your data is on the Internet, attackers can access the information if they really want to. However, they still can’t possibly know your IP or location because your data coming from Tor network, not your house or secret hideout. But fear not, to eliminate this problem somewhat, Tor foundation provides “Tor Browser” for free, which is a modified version of Firefox that, among other things, attempts to use the encrypted “https” standard instead of regular “http” for as much web activity as possible and also disables certain plugins that can leak your IP address and location.

Many plugins, and other applications for that matter, won’t run over Tor network by default and can thereby giveaway your identity even if your other traffic, normal web browsing traffic, is going through Tor. It is possible to force other applications to use Tor network either by manually configuring them or using programs like “Tallow” to do it for you but since any unencrypted information that you send or receive can still be seen by exits nodes, some users have tried using virtual private network (VPN) in conjunction with Tor to create an encrypted tunnel at every point of the connection, as long as you can trust your VPN provider. But of course, the best idea is not to send anything personally identifying over Tor or anywhere if possible.
What Are The Drawbacks Of Using Tor?
Tor also has the limitation of being a rather slow network so it might not be useful for downloading large amounts of data, streaming or using BitTorrent. Especially BitTorrent protocol can broadcast your IP address if you aren’t careful.
Should You Use Tor To Browse The Internet?
If you’re casual Internet user and signing on to Facebook or social media, probably not because you’re putting identifying information out there anyways. But if you are living in a country like Turkey where people can get arrested for posting a tweet or if you’re looking to score some weed and read ProPublica, then yes you should use Tor.
If you ever decide to use Tor, their website is https://www.torproject.org/